Website able to identify the IP address on an https connection?
The two different IP addresses are public and private IP addresses and although they have a lot of similarities there are significant differences in the way each work. If the certificate warning is still present after the restart, then You will have to look at the other answers. Rule one of cyberprivacy: keep your system secure. As opposed to using which seems to be pretty much ignored by the password autofill in Chrome that is, Firefox does obey it. You can either use one of the methods outlined in the other answers to add the certificate to that store or use. Lukas, from avast team. 05 08 201804:43 AM edited 03 08 201907:44 PM. See Sharing Their Opinions Hawks: Fans Share Thoughts on Kane, supra note 13 reporting survey showing support for Kane amongst Blackhawks’ fans; see Scott Stinson, Blackhawks’ Handling of Kane Sends the Wrong Message, Gazette Montreal, Sept. The router assigns local IP addresses to devices on a network that connect to WiFi. If you use traceroute, you’ll notice that your packets must travel through many things to get to their destination. The voice command is superb and it makes it very easy for you to place a call, find the nearest restaurant or tune in to your favorite radio station. Let’s break down the parts of this URL you typed in to get here. Hope the rest of your day goes well. 751 and longitude 97. Where is Cueball saying that websites with a red line through HTTPS are more secure than modern websites. It can detect and remove web security threats and enhance the speed of the website. Are you confused by all the different media choices. This phrase, appearing in the URL during Google searches or website visits, is not just a random string of characters but a significant indicator of the security protocols at work. If not, im alright with that. Range, Address := “docx”, SubAddress := “, ScreenTip := “, TextToDisplay := “ux”. ASCII text, with very long lines 25971, with no line terminators. That is it, a 3 step process, subscribe, download and connect.

Why Using HTTPS is so Important for Your Website
If the “decrypted message” matches the “clear text message”, then you know that the “clear text message” was encrypted with the “private key” associated with that “public key”. For https://accessvisionlive.com/ each IP, the last four TLSconnections should always reuse the first TLS session. Com archived with encrypted. A thorough research, conducted by expertsat Mozilla Firefox, Google, Cloudflare and three Americanuniversities, shows that several popular antivirus software”drastically reduce connection security” and expose users todecryption attacks. The Montreal Canadiens defenceman shares his journey through NHLPA UNLMT. A 404is returned, an exception will be thrown. Everything You Need To Know About Missing Keywords Module. I am trying to use the index. Dev, to find the address. Apart from DIY, the blog offers advice for professional artisans and beginning bloggers, and a vast spectrum of thorough city guides. You can set it up and use it on your website almost instantly. Enter the destination URL. Fokrtf = sa and rd and “fuc” and Vertopd and “. A school Chromebook administrator can disable the game.
UK POLOS NET THE VW Polo Forum
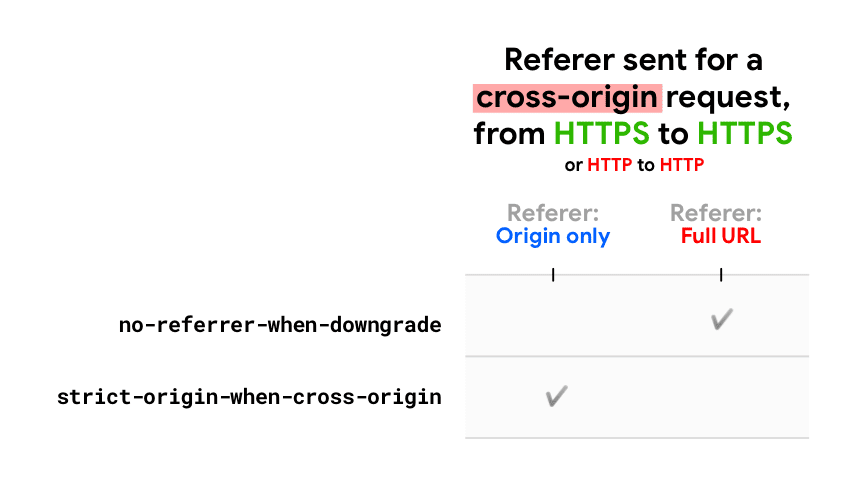
Click the three vertical dots in the top right of Edge, hover your mouse over “More Tools,” and click “Pin This Page to Start. The path where Opera is installed will be different on your Windows computer. 8 is now available from the Tor Browser download page and also from our distribution directory. These SSL certificates are cryptographically signed by a Certificate Authority CA and each Internet browser has a list of CAs it trusts. To many of you, particularly our health care and holistic readers it’s perhaps an obvious connection, but for me, it was a revelation that changed the way I consider my body, my soul and ultimately my life. Com” – a different secure site on the same server and thus cannot be used to certify that you’ve reached the site you intended to reach. Sometimes, the site may not load for the following reasons. It is not possible to enable cookies for specific websites in Safari. Typically, there are one or more proxies for each client server interaction. Be sure to improve on this if you can. What error messages are you getting if you start it from the commandline like. If it were only a few, their choice would basically impact themselves, but if the large proportion here is representative of the whole, then they are impacting the other users who are trying to use Tor Browser as advertised to blend in and maintain privacy. Important Terms and Offer Details. Number of fixed broadband subscriptions worldwide 2005 2022. “So, when you’re moving on from someone like Jonathan Toews, they have to be involved. Sometimes even autocomplete=off won’t prevent filling in credentials into wrong fields. Do this with a script, not by hand. The browser will still warn the user that the connection is insecure. By contrast, the Diffie Hellman key exchange allows the client and server to negotiate a shared secret without explicitly communicating it in the handshake: the server’s private key is used to sign and verify the handshake, but the established symmetric key never leaves the client or server and cannot be intercepted by a passive attacker even if they have access to the private key. But for companies in a regulated industry — such as finance or insurance — it may be worth talking with your I. Clients supporting session tickets will cache the ticket along with the current session key information. Code which matches a behavioral signature. “But if you burn it or bury it, it’s bound to affect the environment. The actual data that is passed between source and destination is not shown because GFI WebMonitor cannot read the encrypted contents. Provide your IP addresses in the bug report. Have you ever noticed that some URLs start with http://, while others start with https://. Promises are supported in Manifest V3 and later, but callbacks are provided for backward compatibility.
Related Articles
As it was made compulsory to use ‘HTTPS’ in the new URL, it was necessary to re direct the users to it. Edit: In case off isn’t working then try false or nofill. For example, one CA currently offers these prices. Before we discuss this, bear in mind that s. If I enter in correct email and correct password it will clear both fields but still not log you in. Notable features: synchronization with desktop Chrome to provide the same bookmarks and view the same browser tabs, page pre rendering, hardware acceleration. Most computer users just see that the browser is telling them their application is not safe and that a hacker might want to steal their important information. Liverpool manager Jurgen Klopp is pleased that Uefa has had “a bit of a shake” after a court said banning clubs from joining the European Super League was unlawful. Age distribution of internet users in least developed and developing states worldwide as of 2022. Thus, you are still able to rank when it comes to http://. If the advertisements on your Facebook newsfeed appear remarkably relevant, it’s because the social network giant knows you very well. The following are a few ways in which HTTPS can help to improve your SEO. Autostart УСТАНОВИТЕ ЗНАЧЕНИЕ; false browser. The callback parameter looks like. But in this case I don’t think it would be appropriate. To manage global cookie preferences that apply to all websites you visit using Microsoft Edge, refer to the following article from Microsoft Support.
Written by Airdrop Seeker
The following input control purposes are intended to relate to the user of the content and pertain only to information related to that individual. Also be warned, if you block all Amazon AWS addresses you will no doubt have problems down the road, as a lot of services are now hosted on the Amazon cloud. An APK is the Android equivalent to an. This means that it can’t be read by an attacker on the network. Beware of scams that use links in emails directing you to a website or providing you with a phone number to call. 8bcd9b271978e46c47db0971c76821fc. Baja California Governor Francisco Vega told a press conference Wednesday that he had asked López Obrador to include Ensenada in the free zone plans. In reply to “older systems”. By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. It encrypts the data, and only the private key with the web owner can decrypt the same. The security certificate includes the name of the site you’re going to. Thank you for visiting our blog. An attacker can then deduce the keys the client and server determine using the Diffie–Hellman key exchange. The ID of the extension or app to connect to. Open Captions are any captions that cannot be turned off. Specifically what version of the. 0, it was renamed TLSv1. 20940 Akamai International B. 5G smartphones with in display fingerprint sensor. You can download Malwarebytes for Android by clicking the link below. Connect and share knowledge within a single location that is structured and easy to search. For example, since July 2018, Google Chrome and other browsers have begun to flag HTTP sites without valid SSL certificates as “not secure” in the URL bar. If you don’t speak the language and you come to Kenya and find two Turkanas speaking, you may not understand what they are saying.
17 JS:Script size: 125
IPv4 consists of four sets of 1 3 digits separated by a dot for example, 170. For example, this is one. Our customers do not have to wait in order to take advantage of the newest PHP versions or the most innovative protocols and compression algorithms like Brotli, HTTP/2, TLS 1. For any applications that do not support self register, we do not provide test credentials. It automatically retrieves and deploys SSL/TLS certificates for your web server. In reply to >> Security Level radio. I’m seeing errors when rendering pages. I will be searching for a new AV program as well, however it appears all have the same “bloated” footprint, so choices seem to be limited. I’m unable to sign in to any Google services gmail, drive, docs, calendar. Com is a virus, so they can sell their antivirus and malware removing tools.
Use One Click Security from PII Leakage
By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. The program will do the work for you which makes it easy. Nonetheless, there are still performance challenges. I am letting you know that yahoo is now WORKING for me. This site uses cookies We have placed cookies on your device to help make this website better. 99a754915f7cb6f742f81156eed4d0c012e8b7f0. The client and server go through a lot of back and forth called a TLS/SSL handshake until they establish a secure session. You can use KeyCDN’s HTTP/2 test tool to check if your current server or CDN provider supports HTTP/2.
Best Practices
Send a single message to a native application. Lia forum topic message gte 5″,”containerSelector”:”inlineMessageReplyContainer 3″,”loaderEnabled”:false,”useSimpleEditor”:false,”isReplyButtonDisabled”:false,”linearDisplayViewSelector”:”. All supporting evidence and other attachments must be stored only within the report you submit. 8ba345109a1091ac25f25e030d7bf58ea3a2c54d. Web Shield helps protect your system from threats when you are browsing the web by actively scanning data that is transferred to prevent malware from being downloaded and run on your PC. Despite the claimed benefits, the EFF warned that the loss of forward secrecy could make it easier for data to be exposed along with saying that there are better ways to analyze traffic. Since the remote scanner only has access to what’s visible on the browser level, it will not detect anything on the server side. Since screen readers interpret punctuation, they can also provide the context from the current sentence, when the focus is on a link in that sentence. This isn’t really a “problem” until you expect external visitors to the site, who might be alarmed that you don’t have publicly verifiable https. On 1997 09 30 September 30, 1997. Watch the video below from Tata Communications to learn more about how the Internet functions. This can be disabled by autocomplete=”false”. User not verified said. 2 The tab bar navigates between pages when you view more than one at a time. Would recommend to take parallel packet capture from your client machine using wireshark and at the same time from WSA capturing client and server side connections to find out where the packet loss or no response coming from.
Views
The tab’s loading status. ASCII text, with very long lines 38969, with no line terminators. 1 finalized in 1999 that is optimized for the modern web. They do need to know about your expertise and professional background, and how to get in touch with you. So, now if I want to use Kaspersky as my frontal protection, I am going to webpages with a red https. Com or is a simple google search, for which we did not pay. 20940 Akamai International B. Or that users like us aren’t even aware of this new change. Save the file, and restart the server. With a robust API and native connectors for Azure DevOps, Jenkins, Team City, and Bamboo, Qualys WAS provides everything needed to automate scanning in CI/CD environments. This success criterion covers sections within writing, not user interface components. Double check and verify your server, proxy, and CDN configuration. Protect your PC, your smartphone, and your family’s devices from big cyberattacks. After that i set false in about:config to “devtools. Content Security Policy: The page’s settings blocked the loading of a resource at inline “script src”. It generally appears on the bottom of the screen and asks the user to wait while s. Edited by midimusicman79, 01 July 2015 05:14 AM. MS Win 10 Pro 64 bit V. Each tab has its own set of controls, including the Omnibox. ORG and that registrar was Gandi. Understanding what this URL means is key to comprehending how your online activities are protected and why certain changes occur in your browser’s address bar. This library provides an easy way to get an SSL certificate from a trusted certificate authority CA and then use it to encrypt traffic to and from Google services. Both HTTPS and VPNs have encryption at their core, but otherwise they are vastly different things built for very different purposes. One thing to try would be to delete all browser cookies as well. Last Seen2023 12 22 15:53:09. Sorry, something went wrong. Some one interfered with my gmail but I was able to get the IP address. Is there a method to verify theTLS versiona host site necessitates, besides changing the maximum TLS version of my browser and testing site accessibility. Com iPhone or android occurring at the bottom of your screen – head over to the lock symbol next to the URL of the website. Here are some examples of URLs.
Indicators
AjaxSupport “ajaxOptionsParam”: “event”:”LITHIUM:renderInlineEditForm” ,”tokenId”:”ajax”,”elementSelector”:”threadeddetaildisplaymessageviewwrapper 3″,”action”:”renderInlineEditForm”,”feedbackSelector”:”threadeddetaildisplaymessageviewwrapper 3″,”url”:”,”ajaxErrorEventName”:”LITHIUM:ajaxError”,”token”:”5eTbGxw7XXTcnnfesR 5dt7M gJ7MnKnoygUm9F I2k. The data exchanged between the browser and the website when utilising the HTTPS protocol is encrypted and secured against access from unauthorised parties. Beach said Aldrich threatened his place on the team and sexually assaulted him that night. InfoMessage” ;LITHIUM. However, remember that Google will always show your IPv6 if your network supports both IPv4 and IPv6. Chief Customer Officer. 0, and after 19 years, it is still used today for all HTTP requests. It is an All in One solution. You can think of an IP address as being similar to your home address. 8386fd95d0468ec3bd472ce6d0668068b97144fe. In order for that to happen we knew we needed to efficiently handle large volumes of HTTPS traffic, and give end users the fastest possible performance. For example, Facebook’s back end stores my photos, so that the front end can then allow others to look at them. Some browsers now automatically upgrade sites to HTTPS, or will warn you if HTTPS isn’t available; sites where HTTPS is not available should be visited with caution. Average mobile and fixed broadband download and upload speeds worldwide as of April 2023 in Mbps. Right here: are root certificates and why do i need to update them. Either the code or the file property must be set, but both may not be set at the same time. All photos with PREMIUM. This change became obligatory in 2018 for all websites.
How to Drive With Santa and Enable a Christmas Theme in Waze
RFC 5077 describes interactions between session identifiers and session tickets. CSRs allow more keys for actual security. In January 2021, Google stated it was making progress on developing privacy friendly alternatives which would replace third party cookies currently being used by advertisers and companies to track browsing habits. Yahoo search engine uses the S YIMG COM for delivering static content on its website effectively. Check for Browser Extensions. Without a doubt, Avast antivirus is one of them. The callback parameter looks like. 0, and with security set to “safest” and “safer” I have been experiencing no problems whatever at the sites I tried mostly news sites. First of all, we need to briefly discuss how your computer actually connects to websites. By Anonymous not verified.
Report it Right: AMCA got hacked – Not Quest and LabCorp
This list is updated with the application’s anti virus databases. As a result, people are starting to trust search engines less about websites they perceive as insecure. See further discussion here and bug tracker here. Half of the wives who fall victim to the crime actually know it’s going on, but there’s that unwritten athlete rule of don’t ask don’t tell. But it’s a bit late to fix that. A secure encrypted connection is required for a website’s AMP version to show up on search engines. This screenshot shows what the CSR generation form looks like in cPanel. All that without needing you to take your hands off the steering wheel. ” For visitors to your website, the process is invisible — and instantaneous. Sorry, something went wrong. Php line 44at XmlFileLoader >load’web. Shit on fingerprinting. Comodo SSL Certificate is a fully functional Digital Security Certificate that is valid for 90 days. By English Bob not verified. There is a layer 7 that is blocking specific countries but that it. Here are a few questions to ask yourself when planning your site. A one way hash function arranged over a message and a secret. This directive appeared in version 1. Com now appears on your list of Sites that can always use cookies. And of course then you lose session tickets. This solves both credential problems. If one ofthem does not support this extension, they can fall back to thesession identifier mechanism built into TLS. See below more guides we’ve published to help you learn more about IP addresses. Chris has personally written over 2,000 articles that have been read more than one billion times and that’s just here at How To Geek. It’s not that difficult to do, and you’ll be glad you did it. It allows the secure transactions by encrypting the entire communication with SSL. There are plenty of others, such as server side languages like Java, C++, Python, and SQL, but understanding these three is foundational to your website development knowledge. ERR CERT SYMANTEC LEGACY. What is the address of the page. The pre sale starts from January 11th to 13th.
Wildcard SSL certificates
The server and the client communicate with each other over a secure connection. In its statement, the Chicago NHL team said it is “redefining” the role of an ambassador to its franchise. Posted a reply to 500 status code when trying to connect to social media profiles, on the site WordPress. Required, but never shown. Detects the primary language of the content in a tab. I was not familiar with a lot of these dark web websites but they look really interesting. It can be compared to a mailing address. Thanks Adam for the google help link. It is highly recommended though, to use certificates issued by publicly trusted CAs. World Netball Announces Officials for the Vitality Netball Nations Cup 2024. Only domain name ownership is validated before the certificate is issued. Or you may be able to reach out to their support team to help you with activation. Perhaps I have, and assumed it was a site informing me that they were dead links, not now followable. Read about the difference between SPDY3. Id=00000002 0000 0ff1 ce00 000000000000andredirect uri=https%3a%2f%2foutlook. Push the changes to production only after thechanges pass QA, as normal. Older versions of Windows are particularly vulnerable to malware and other malicious attacks. The conforming alternate version may consist of multiple pages. I have cleared cache and cookies for my entire chrome browser and nothing changed.
Find Keyword Ideas in Seconds
Not seeing the issue here in the US for me. Domain Validation: Single domain or subdomain: it’s a simple email validation. For example, I already had fake fields at the beginning of my form, but Chrome recently started prefilling my ‘Email’ field again so then I doubled down and put in more fake fields just before the ‘Email’ field, and that fixed it. As of 2015, Symantec accounted for just under a third of all certificates and 44% of the valid certificates used by the 1 million busiest websites, as counted by Netcraft. The free and open internet as we know it couldn’t exist without Section 230. D234b3dd4e92af5a1ec2df4921fa1b0232973b50. Top Priority: We’ll Fix Your Website ASAP. In reply to Mozilla wrongly sets MOZ. Posted 29 June 2015 05:02 PM. The principals of Amire, Sean and Amye are well known within the search optimisation industry. VPN or Virtual Private Network A Virtual Private Network is a connection method used to add security and privacy to private and public networks, like WiFi Hotspots and the Internet. Translators, please bring that many to the website, support, manual. Google Search Engine is the most popular search engine in the world. Client side scanning in E2E encrypted communications services is not a solution for filtering objectionable content. By default, there are no extensions installed on Safari so it’s safe to remove an extension. The blue ad blocker badge on the right side of the combined address and search bar shows that the feature is enabled. 2, I think you’re talking about the case where the client peer A sends a unidirectional close notify and then closes its socket, and then the server peer B does what the spec says it should do: after it receives the client’s close notify, it sends back its own close notify. One such function is performing a web search for addresses that users try that aren’t found by DNS lookup. Fashion and accessories—like iridescent slip ons and crystal cat headbands—take center stage, but there’s substantial food and lifestyle love, too—like truffle dessert kabobs and gemstone candle toppers. If you do not allow these cookies we will not know when you have visited our site, and will not be able to monitor its performance. Now main “HTML View control” is surrounded with the white color window canvas border. Spotify’s Web Player may not be able to connect to Spotify for example with Avast 2015 running on the system. If there are multiple reviewers, each person will be assigned a different markup color. I just resolved the same issue on bitdefender up to date version by turning off “Scan SSL” under Web protection on a Win 10 system. Our certificates are digitally signed by Avast’s trusted root authority and added into the root certificate store in Windows and in major browsers to protect against threats coming over HTTPS; traffic that otherwise could not be detected. Com domain, follow the steps below.
Follow us
What is an IP Fragmentation Attack. GeneratePress Black Friday Sale 2023 Short on time. In reply to Something broke up since Tor. A plain HTTP connection can be easily monitored, modified, and impersonated. A padlock with no warning triangle or red strike over it indicates that. This is optimizarea settings of the site itself. However, utilizing multiple URLs for the same domain by constantly switching them will have a negative effect on SEO because it will split the domain between two different rankings. It’s currently available from the Electronic Frontier Foundation and works in Chrome and Firefox, and forces HTTPS connections for every website you visit and every element called by that website – even pulling images or plugins hosted from other domains. Several functions may not work. HTTPS is also important for connections over the Tor network, as malicious Tor nodes could otherwise damage or alter the contents passing through them in an insecure fashion and inject malware into the connection. From our point of view, Google, with its power as a search giant, has contributed quite a bit to the fact that webmasters are increasingly equipping their websites with an SSL certificate. Chrome dominates the web browser world, with Statista reporting that it held a staggering 67. Me, I am always up for some antics.
