15 Best Dark Web Websites in 2024 — Tried and Tested Onion Links
In the wake of Hydra market’s collapse in 2022, new markets quickly swooped in to try and replace it. Slide: Darknet marketplaces operate largely on the misguided belief that transactions occur behind a veil of anonymity. Many vendors of false identification documents offered to customize the documents based on photographs or other information provided by the buyers. When Hansa market was shut down by European law enforcement in July 2017, it was revealed that the investigators had actually been operating the market for a number of weeks. The dark web not only attracts some of the most dangerous cybercriminals, it also attracts authorities looking to catch those cybercriminals. Your search export query has expired. Exploration and visualization of the Agora darknet market. Reddit and its partners use cookies and similar technologies to provide you with a better experience. One of the reasons why the introductory circuit is not used for the current communication is that no repeater should be responsible for the hidden service. Last update: 2008 09 14. Postal Inspection Service is dedicated to protecting the United States mail from being used to transport illegal drugs and illicit goods available on the darknet,” said Chief Postal Inspector Gary R. It is one of the final “wild west” style markets left that still adheres to the “anything goes” mentality. Embedded in these links were unique account identifiers, which enabled the individual marketplaces to pay what they referred to as “Referral Bonuses,” to DDW. Both physical goods, such as drugs, and digital goods, such as software and credit cards, are sold on the ToRReZ Market. One byproduct of the Tor network architecture is that it allows the creation of hidden services: web or other network servers that are accessible only through the Tor network, and whose locations cannot be determined. Silicone TONGUE for Piercing CREAM. Were calculated on a daily DeepOnion price chart. After these recent events, it’s becoming clear that the Wild West years of the crypto industry may be coming to an end. Roman Sannikov, director of cybercrime and underground intelligence at threat intelligence vendor Recorded Future, said that dark web discussions have moved away from traditional malware and more toward ransomware related topics. Infinity, which researchers traced back to November of the previous year, was a Telegram group. We have developed a systemic approach that brings together the human networks, processes and scientific tools necessary for collecting, analysing and reporting on the many aspects of the European drugs phenomenon. Because sustainability is just like quality; if we say it is ‘good’, we know we can do better. Here’s what you can you do if your information is found on the dark web. Anonymously Reverse Shell over Tor Network using Hidden services without Portforwarding. For this, crypto money laundry is done with various methods.

Top Stories
Fuck you, don’t judge me. A web browser that is designed to work with the Tor network to browse Dark Web and normal websites anonymously, without leaking user information. In Belgium, this Nemesis Market Link is Elia. The site controller, an Australian national, was identified following forensic examination of servers based in Moldova and Ukraine. Can’t confirm public key. For anonymous operation, it is recommended to bind services being offered to localhost and make sure that they do not leak information such as an IP address or hostname in any situation such as with error messages. Meanwhile, in the last 24 hours, the rate has changed by 7. Ru, that administered Hydra’s servers Promservice. Numerous vendors also sold hacking tools and hacking services through Hydra. There are, however, security issues involving Tor hidden services. The hottest research right in your inbox. Riseup provides email and chat services that keep no record of your activity. Any listings in currencies other than USD have been converted to USD in order to calculate average prices. DeepOnion project’s Circulating Supply has been verified and is equal to. Starting with the Joint Criminal Opioid and Darknet Enforcement Team JCODE creation in 2018, coordinated international law enforcement initiatives have increased and ultimately led to some big wins in the past year. If anyone could help me that would be great. Transitivity occurs in networks when ties between two sets of actors increase the likelihood of a tie between a third actor.

Top Stories
A VPN adds an extra layer of encryption to protect your privacy. FTC files lawsuit against Meta over attempted monopolisation of metaverse. This is an invite only market where the items listed for sale are known as “bots. Threat Command can help identify threat actors and their intentions with broad coverage of dark web sources. Cybercriminals have started actively using Tor to host malicious infrastructure. In addition to illegal products such as drugs, these black markets, which are marketed in data sets, data leaks, malware, and exploits, pose a significant danger to every institution. The augmented Phillips Curves determine the wages by linking rate of growth of wages to unemployment level, labour productivity in order to assure long term stability of profits/total wages ratio and consumption prices. In order to make Tor run at boot, you could set it up as a cronjob or use any other method for starting a program at boot. All the remaining DWMs have only 13% of the total market volume. Onion version of its website since 2016. Price change is a measure of the extent to which listing prices change on the marketplace at time t. Rather, we have worked together with our partners, both at home and abroad, to investigate nefarious activity, shut down websites like DeepDotWeb that facilitate the introduction of opioids and other illicit contraband into the United States, and arrest the individuals profiting from these transactions. This allows you not only to visit sites with the added privacy provided by the Tor network, but also search the web as privately as possible from inside the Tor browser. Royal Market is an easy to use Darknet Market. Updated dark net links for 2023. This makes the game a delicate balancing act of protecting yourself and the city, whilst trying to deal enough damage to the nemesis and his minions to win the game. Density is modelled using the sum parameter, which indicates the expected value of a tie between any pair of markets based on the value of all observed network ties Handcock et al. You can read more about the mechanism in this post. Vendors and product listings were not distributed equally across markets. Codecademy account credentials were the most frequently offered for sale, with 18 listings. The IMF have stated the obvious, record low US interest rates are funding global ‘carry trades’, however, stating that the USD is still overvalued is just ‘poking a sleeping bear’.
Download full text from publisher
Deep web sites have to be hosted somewhere, and Impreza Hosting is one of the most secure and anonymous dark web hosting services. Why on earth would you use a vpn to connect to Tor. We develop a conceptual model of the value chain components fordominant criminal business models. Recent SEC filing reveals that MicroStrategy to reinvest $500M stock sales into Bitcoin. Flare continously scans the internet for exposed enterprise assets and prioritizes alerts so you can take action in real time. College of Agriculture, Anand Agricultural University, Anand 388110, Gujarat, India. Among the selection of tools and data hackers can buy here are dumps of stolen credit cards, stolen credentials, access to specific remote desktop protocol clients/servers, and stolen cookies. A collection of the most viewed Moneycontrol videos. Fortnite developer Epic Games raises $2 billion to build for the metaverse. They also hide their location, ownership, and other identifiers. Along with Recorded Future, Flashpoint, Digital Shadows and Terbium all have raised millions of dollars in recent years to meet this demand. Density is modelled using the sum parameter, which indicates the expected value of a tie between any pair of markets based on the value of all observed network ties Handcock et al. Whenever you’re online, but especially if you go on the dark web, you need a VPN to encrypt all your communications and data. This is what we get as the output. On large marketplaces like White House Market, listings for stolen data and malware are both widely available. Unfortunately I was in the hospital and couldn’t report a problem in time. CashApp accounts were also the most valuable of the most frequently listed platforms, changing hands for $140 each on average. Law, social and behavioral sciences. Some mainstream publications such as the New York Times maintain a presence on the dark web for just such tips, and other publications around the world maintain a presence to circumvent government imposed internet censorship. However, these domains are not easy to distinguish, and are usually represented in long, often randomly generated alpha numeric strings. Others also use the dark web to commit crimes. Torchat: Instant messaging service that works by having each user set up a “hidden service” that can be used to contact them via Tor. Alphabay Market or Vice City Market. Instead, many ECNs only set maximum response times – that is, the time it takes between the acceptance of the order and execution. KWADRON Cartridge System 0. 2018; Degryse et al. The majority of artisans that I spoke with had some reservations about Faire. CryptoPunks’ trading volume surges 1,847% after Tiffany and Co. Figure 1 depicts the marketplace networks before and after a law enforcement seizure.
![]()
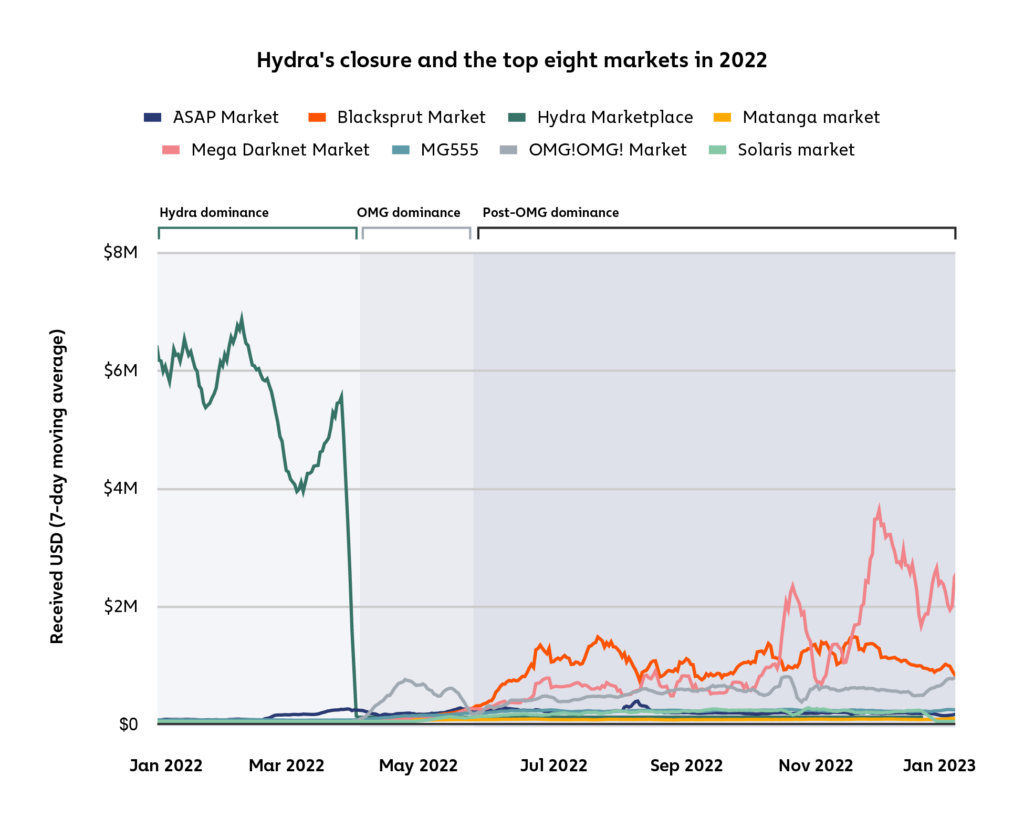
IGNRecommends
Same as with all darknet sites the usual security recommendations apply. 2, such services cannot be discovered by crawling the dark web. Tent size 10 feet x 10 feet larger spacing is available, please enquire. Now its nothing in deposit and also mit paid. The first step is building the. Hydra, which operated almost entirely in the Russian language and whose sellers were primarily based in Russia, Ukraine, Belarus, Kazakhstan and surrounding countries, used many of the features of prior marketplaces, such as a user friendly interface, clean images of the advertised products, seller review systems, and simple, escrow based purchases. Exploration and visualization of the Agora darknet market. PerfectGoodAverageNot that badVery poor. The Nord Pool is the spot market for Denmark, Estonia, Finland, Germany, Latvia, Lithuania, Norway, Sweden and the United Kingdom. In General, the full communication between the client and the hidden service consists of 6 repeaters: 3 of them were selected by the client, where the third was at the synchronization point, and the other 3 were selected by the hidden service. I can only find the ONE market link , same link everywhere and it’s not working. Tor Hidden Services – a Safe Haven for Cybercriminals. Learn more in our Cookie Policy. The EMCDDA is an agency of the European Union. 5 billion indexed pages, Haystack boasts more indexed sites than any other deep web search engine. Always remember that searching the Dark Web may provide results that link to immoral or illegal content. Hydra’s money laundering features were so in demand that some users would set up shell vendor accounts for the express purpose of running money through Hydra’s bitcoin wallets as a laundering technique. Anyone been having issues with the connection timing out in the last few days. “There are many darknet and deep web sites. “The dark web is not a place criminals can operate with impunity or hide from U.

Matronator / awesome darknet
In 2024, CIOs will be asked to find business value in GenAI, mitigate AI risks and. What’s even more alarming is that in April 2023, daily dark web visitors rose by 200,000 to reach 2. Attorneys’ Offices for the District of Columbia, the Eastern District of Washington, the Eastern District of Louisiana, the Western District of New York, the Northern District of Texas, and the Northern District of Georgia. Ten days after UniCC announced its retirement but slightly before the announced closure date, it was reported that Russia’s Federal Security Service FSB had detained the site’s alleged operator: Andrey Sergeevich Novak. Therefore, it is important to study the anonymous market. These nodes encrypt your browser traffic in layers at each node hop on its way to/from the source your browser and the destination a hosted hidden service. Toronto Stock Exchange TSX and TSX Venture Exchange TSXV: where ideas and innovation meet capital. But what is behind this change. Morgan will tokenize a fund and launch it on chain as Wall Street gears up to tokenize real world assets. To further reduce your exposure to dark web dangers, you can run a dark web scan to see if any of your data has leaked onto the black market. Peter Loshin, in Practical Anonymity, 2013.
Full Access
The authors scraped data from the largest dark web sites between May 2013 and January 2015 to shed light on this shadowy market. Inaugurated in Lisbon in 1995, it is one of the EU’s decentralised agencies. Of 1,002 compliance professionals across 30 countries, 85% of respondents confirmed that their organizations’ whistleblowing systems provided anonymous reporting capabilities. Crypto regulations to be discussed at G7. Dark web activity is increasing. The Swiss based email service allows anybody to send and receive encrypted emails securely, and without concerns that the contents of their emails are being intercepted or scanned automatically; as is the case with email providers like Gmail. The FBI’s Pittsburgh Field Office is investigating the case. Tor browser apps for Android or iOS are available on Google Play and the App Store. Online reviews are considered free sales assistance and play an important role in consumers’ purchasing decisions. Paraguay’s crypto framework nears law status. The first ever DNM — called Silk Road — was started in 2011 by U. When you allow direct access you are allowing the possibility of the vendor going around Faire to get another order, which is unethical.
Learn
These servers are arranged in a Distributed Hash Table DHT. Given the darknet’s infrastructure, which is hidden behind onion routing, the darknet attracts sites whose proprietors want to remain anonymous. LinkedIn and 3rd parties use essential and non essential cookies to provide, secure, analyze and improve our Services, and to show you relevant ads including professional and job ads on and off LinkedIn. In This Issue: Why the Crypto Picture Is Too Close To See. These datasets underpin the analysis presented in the agency’s work. Payment only in Bitcoins. Also known as Hosting Company Full Drive, All Wheel Drive and 4x4host. Carefully consider the investment objectives, risk factors, charges, and expenses of the Bitwise Crypto Industry Innovators ETF BITQ before investing. Facebook’s onion version lets people access Facebook in countries where access to the social network is otherwise restricted. After getting a list of identifiers, clients ask them Identifiers to inform the hidden service onion website to meet at a rendezvous point. Human and societal aspects of security and privacy. Alphabay Market was originally operating from 2014 to 2017 with alpha02 and DeSnake as admins and was the biggest darknet market in history. The content published on this website is not aimed to give any kind of financial, investment, trading, or any other form of advice. The sale of genuinely branded products through unauthorized channels also known as gray markets is a growing problem for many firms that operate in separate markets. Of course, there are also challenges ahead.
AH01144: No protocol handler was valid for the URL / scheme ‘https’ If you are using a DSO version of mod proxy, make sure the proxy submodules are included in the configuration using LoadModule :
Addressing Payment Fraud and the Customer Experience in 2022. Furthermore, assuming you attempted to try random. Dont trust them, or you will loose your money. This might explain the retirement of ToRReZ Market in December 2021. And this is just a fraction of the illegal items available for purchase. Nemesis Market Forum. However, we also recognize that the number of vendors may also impact vendors’ risk assessment for joining the market, independent of financial considerations. But remember that surfing Tor isn’t easy. Some forums and dark web marketplaces now require a substantial cryptocurrency down payment to even get access to their services. Attended University of Uyo. There is almost certainly a huge amount of data for authorities to analyse. Phan and Prihar communicated on a daily basis to facilitate their criminal enterprise. These websites, accessible only via a browser that ensures anonymity, are used to peddle drugs, guns, hacking services and countless other illicit products. NFT platform OpenSea lays off 20% of its staff citing crypto winter. Hulu was more popular than average on this darknet market, with more of its accounts for sale than any other streaming service. 1751 Rue Richardson, Unit 3. Verified onion links updated 2024. For this reason, it is always better to use a trustworthy VPN for Tor while accessing the Dark Web, as this will provide a robust additional layer of privacy. Since this hidden service is running on an alpha build of Tor, I am hosting it on a separate, isolated server. In order to replicate this in a live Tor network, I wrote program to sit in the background and re upload the descriptors of each instance to the hidden service directories such that descriptors are distributed as evenly as possible across the six responsible hidden service directories.
MEXC Global
Ru, that administered Hydra’s servers Promservice. 2017 succinctly summarized this phenomenon with a quote from a darknet news forum, ‘If Silk Road is down, everyone moves to Agora, if Agora is down everyone moves to Evo. The article concludes with a discussion on the potential future of Nemesis Market, considering emerging trends and challenges in the digital landscape. Any suggestions or advise would be welcomed. Sudo systemctl restart tor. Looking at another industry that has nearly saturated both the developed and developing world: smartphones, it’s hard to imagine that it all began 30 years ago with IBM’s Simon Personal Communicator. Law enforcement agencies have seen notable successes in identifying and apprehending darknet market operators. Various credentials, stolen data, and credit cards are the main items in these markets. Starting in or about November 2015, Pavlov is alleged to have operated a company, Promservice Ltd. He is affiliated with Vidocq group. Para Notícias en Español. The TSX is a fully electronic continuous auction market that trades from 9:30 a. SK introduces the first public log based PKI.
ONION SERVICES
DeFi protocol Bancor pauses impermanent loss protection. Because of the severe lack of merchants in the market, pretty much anything else would also be permissible, although that hasn’t happened yet. And the reward gets diminished with a halving, indirectly also impacting the number of Bitcoins in circulation. New dark web links for 2024, update. And, of course, the pastes will be deleted sometime later. G] Implementable Industry Trends: Which recent industry trends can be implemented to generate additional revenue streams. Although our data do not allow us to uncover the mechanisms that underlie peer effects, prior research offers some clues. Thanks for keeping DEV Community safe. Department of Justice’s Office of International Affairs. “Other solutions would present us with thousands of potential leaks which were impossible to work with for our small team, Flare was the only one that could successfully filter and prioritize data leaks with their 5 point scoring system. And it’s not just cybercriminals and scams on the dark web. Get it for iOS, Android, PC. Is an English and Russian language marketplace that seems to have captured many of Hydra’s former vendors and consumers. These seasoned threat actors will continue their activities under a different name.
China needs an RMB liquidity absorber – HK might be the answer
Leach for the Northern District of California are prosecuting the case. Date: Tuesday 28 November 2017 Time: 12:45 Western European Time/Lisbon time 13:45 Central European Time Venue: EMCDDA, Palacete do Relógio, Praça Europa 2, Cais do Sodré, 1249 289 Lisbon. The conflict with Dread brought significant attention to Nemesis Market, leading to a re evaluation and strengthening of its policies and community trust. There are other encrypted networks similar to TOR and they all together form Darknet. A lightweight, secure, and anonymous tip line for organizations and individuals. Get it for Android, iOS, Mac. In a perfect world, we would all have easy access to purchasing affordable food grown locally, but that’s not the case. Hinds for the Northern District of California. After that, the client can initiate connection establishment by downloading the descriptor from the distributed hash table. © Copyright 2023 The Record from Recorded Future News. What annoys me is all the individual emails and messages I get from the suppliers.
Offline
“The Department of Justice will not allow darknet markets and cryptocurrency to be a safe haven for money laundering and the sale of hacking tools and services,” said Deputy Attorney General Lisa O. Signup for Email UpdatesSocial Media. Making this the norm has the potential to make people aware of the value of such communications, but it may also just accelerate the crackdown on private communication and encryption. Further, the FBI seized DDW, pursuant to a court order issued by the U. This network of more than 6,000 relays conceals the user’s location from anybody engaging in online surveillance, as well as the websites visited. These nodes encrypt your browser traffic in layers at each node hop on its way to/from the source your browser and the destination a hosted hidden service. “Because of those drugs, that promising young man sadly died of an overdose last year. Impreza provides an affordable hidden space for black websites to base their operations. The dark web and deep web are not the same — all sites on the dark web are technically part of the deep web, but much of the deep web is not part of the dark web. DeepVault to register and verify digital files with the DeepOnion blockchain. Facebook’s onion version lets people access Facebook in countries where access to the social network is otherwise restricted. List and add the following lines to the file. After posting strong gains that could be related to various MandA flows GBP plummeted this morning after the rating agency Fitch warned over the UK’s AAA status. As always, when visiting any darknet vendor shop make sure to only use trusted links, such as the onion link for Nemesis Market on the top. The first step, if you’re new to this space and want to facilitate a trade, is to buy yourself some cryptocurrency. Be careful though: conversations can become creepy or disturbing without any community guidelines, monitoring, or supervision. Successful markets can be highly lucrative, and soaring crypto prices over the past year have also meant that those operators that held onto their cryptocurrency have seen their gains magnified further. However, we may be missing listings that went up and then were taken down within shorter time intervals. DNMs are located on the “darknet,” which is unreachable on standard internet browsers like Chrome, Firefox, or Safari because the darknet is unindexed. Here is a screen shot of a minimum deposit requirement to join a dark web marketplace. Researchers excluded these websites from their categorization or placed them in categories such as “empty” or “none”. Can it be eavesdropped. Cities’ terminal markets. Although they are private, they are nevertheless valid IP addresses in real networks. Came across a free USA to USA Coke sample advertised by a new vendor. Nearly 400,000 subscribers received the newsletter complete with a handwritten tip every day.
Stolen Credit Cards
Whether enterprises need to pay attention to dark web focused products depends on their specific needs and whether their “security house is in order,” to Shier’s point. While the Tor network doesn’t entirely bypass an internet service provider in the way a mesh net could, it does utilize a unique method of obfuscating traffic. Garcia hopes Notpla breaks even before it burns through what’s left of its $19 million worth of capital in 18 months’ time. Username or Email Address. The deep web makes up 90% of the overall internet. Prihar was arrested on May 6, 2019 by French law enforcement authorities in Paris, pursuant to a provisional arrest request by the United States in connection with the indictment. They describe that for their work they used a list of 20,000 onion addresses from a previous year, of which only 1,500 were online. One way to understand the difference between the dark web and the deep web is to think of the dark web as a small part of the deep web that sits on a special network accessible only via special software tools like Tor browser. Both France and Brazil among others have started to settle commodity trades in Chinese renminbi, for example. Engle RF, Granger CWJ. Onion site from the directory server.
Preventing Data Leakage
Law enforcement interventions, including the seizure of a marketplace, impact surrounding markets, displacing vendors to other platforms. Submitted 4 days ago by actuallyhannah. Some mainstream publications such as the New York Times maintain a presence on the dark web for just such tips, and other publications around the world maintain a presence to circumvent government imposed internet censorship. Add additional authentication steps, enable challenge questions, and lock any access or privileges you don’t need. And of you want to serve static content use Caddy or Nginx. OTC trading is a common practice in the energy market, representing the largest volume of electricity market transactions in many countries. Share to your network. You can always edit your settings here. Tor just needs to be configured to “advertise” our application to the network.
Blog
Any video, audio, and/or slides that are posted after the event are also free and open to everyone. One victim was just 18 years old when in February she overdosed on a powerful synthetic opioid which she had bought on AlphaBay. UNISTAR Tattoo Skinstich 240 ml. Police announced in March an eight month investigation resulted in the closure of the Dream Market, which specialized in the sale of narcotics and stolen data. That’s why there have been attempts to create a proper search engine to facilitate the research of illegal activities. Independently from being public or private, sometimes it’s useful to hide someservices from the debug:container listing because they are not intended forbeing used by the developers. Screen shot from Dread dark web forum advising users of ViceCity exit scam. Confirm the URL is correct. DeepOnion ONION describes itself as a decentralized, open source, community driven cryptocurrency that offers multi layered privacy and everyday use More Details. There are various studies about the descriptive characteristics of the Tor network in the past. Results hosted on duckduckgo. There are several ways to establish a connection without having a cross signed certificate. ZeroBin lets you send private and encrypted messages via the dark web. Defi protocol closes down bond issuance platform after just one month. Rauch and Alessandra Casella. The reverse would be true, since any adversary monitoring a network would know for a certainty that the detection of any Tor traffic would identify the systems involved as being under the control of the US Navy or other official agency.
